Xcomm | Time to review your cyber security
As the number of cyber-attacks is increasing year on year, with one in five businesses losing money, data, or other assets, it’s time for businesses to review their cyber security.
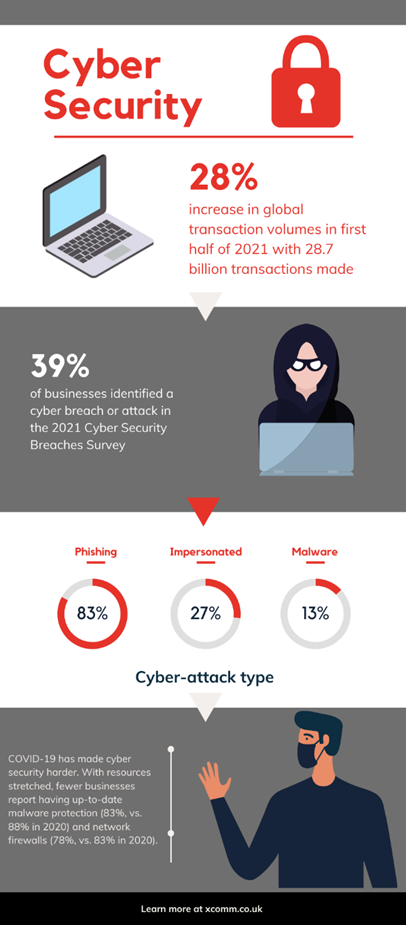
Since the start of the pandemic the amount of time spent online has dramatically increased with a 28% increase in global transaction volumes year on year in the first half of 2021 – with an enormous 28.7 billion transactions made between January and June.
This, in turn, has led to an increase of 41% in automated fraud attempts, with 683 million aimed at financial institutions alone.
What is the greatest cyber security threat?
According to the UK Government’s Cyber Security Breaches Survey 2021, 39% of UK business reported a cyber security breach or attack in the previous year and over 80% of cyber attacks come via email. As cyber defences such as firewalls and VPNs improve, helped significantly by the move to the cloud, phishing emails – particularly business to personal email – has become the main security weakness.
Automated attacks
Automated BOT attacks are also an attractive attack strategy amongst fraudsters globally as there is no language barrier and a very high volume of stolen credentials can be tested on multiple businesses simultaneously. And, because there is no victim interaction, automated bots can operate under the radar without arousing suspicion with their targets.
Get protected
It is important for all businesses to identify and address the cyber security threats they face today. The National Cyber Security Centre recommends you start by reviewing your approach to risk management then implement appropriate mitigations and put plans in place on how you will deal with cyber incidents.
And, to help businesses to achieve this, it has come up with 10 Steps to Cyber Security:
- Risk management Take a risk-based approach to securing your data and systems
- Engagement and training Collaboratively build security that works for people in your organisation
- Asset management Know what data and systems you have and what business need they support
- Architecture and configuration Design, build, maintain and manage systems securely
- Vulnerability management Keep your systems protected throughout their lifecycle
- Identity and access management Control who and what can access your systems and data
- Data security Protect data where it is vulnerable
- Logging and monitoring Design your systems to be able to detect and investigate incidents
- Incident management Plan your response to cyber incidents in advance
- Supply chain security Collaborate with your suppliers and partners
Following these steps should ensure that technology, systems and information in your organisation are protected appropriately against the majority of cyber-attacks and enable your organisation to best deliver its business objectives. However, if this is something your organisation is not geared up to implement then an expert external service provider is the solution.
Help from the experts at Xcomm
Xcomm offers a broad range of secure remote access solutions, market-leading data protection products and related professional data security services – all designed to help your organisation safeguard its business processes and stay compliant with regulations and best practice.
Our skilled IT engineers are available to provide advice on all IT matters including computer and internet security, computer software, cloud solutions, IT support and managed services such as VOIP and website hosting.
Xcomm is a Microsoft Partner and a Microsoft Office 365 consultant. Xcomm also partners with Cisco, Ping Identity, Pulse Secure, Swivel Secure, Juniper, Paloalto and RSA.
Check out our sister company and other brand LineBroker